2021. 2. 21. 18:30ㆍ카테고리 없음
Jul 21, 2013 For many people, the first sign that their email has been hacked comes when a friend shoots them a text or an email saying, 'Hey there. Uh I think your email was hacked. Feb 14, 2014 If you use an email program, something like Outlook, Windows Mail, Mac Mail or you get your email on a phone or tablet computer, you will have to. Nov 11, 2017 A non Jailbroken iOS device can not be hacked, the apps are sandboxed; meaning not only are they available only after validation from Apple as not being malicious and distributed only though the App Store the developers have to use a platform that restricts what their code can do on the device. As long as you do not jailbreak the device this is.
However, it often limits access to apps on TVs to paid Premium subscribers only. https://cleverlocker.weebly.com/spotify-app-on-samsung-smart-tv.html.
Mac Email Hacked Account
Signs your Apple ID has been compromised
Your Apple ID might be compromised if you receive an account notification from Apple for a change you didn't make, or if you notice account details or changes you don’t recognize. For example:
- You receive an email or notification that your Apple ID was used to sign in to a device you don't recognize or did not sign in to recently (for example, 'Your Apple ID was used to sign in to iCloud on a Windows PC').
- You receive a confirmation email from Apple that your Apple ID password was changed or your account information was updated, but you don’t remember making any changes.
- Your device was locked or placed in Lost Mode by someone other than you.
- You see messages you didn't send, or items you didn’t delete.
- You see charges or notices for purchases that you didn't make. Learn what to do if you see an unfamiliar iTunes Store or App Store charge on your credit or debit card statement.
- Your password no longer works, or it might have been changed or locked.
- You don't recognize some or all of your account details.
Serum plugin download. If you received an email, text message, or phone call that you're not sure is valid or you think might be phishing, here are some tips to help determine its legitimacy.
Gain control of your Apple ID

If you think your Apple ID is compromised, use these steps to gain control of it and review your account information:
- Sign in to your Apple ID account page. If you can't sign in or you receive a message that the account is locked when you try to sign in, try to reset or unlock your account.
- Change your Apple ID password and choose a strong password.
- Review all the personal and security information in your account. Update any information that isn't correct or that you don’t recognize, including:
- Your name.
- Your primary Apple ID email address.* If you need to change your email address, update the features and services that you use with Apple ID, so that each one is using your updated Apple ID.
- All alternate email addresses, rescue email addresses, and phone numbers.
- The devices that are associated with your Apple ID, if you've already set up two-factor authentication.
- Security questions and answers. If you think they might be easy to guess, you should change your security questions.
- Check with your email address* provider to make sure that you control every email address associated with your Apple ID. If you don't control the email addresses associated with the Apple ID, you should change the password for the email address or use a different email address.
- Set up two-factor authentication for your Apple ID. This additional security feature is designed to prevent anyone from accessing your account, even if they know your password.
* In China mainland and India, you can use your phone number as your Apple ID.
If you completed the steps above and think your account might still be compromised, contact Apple Support.
Know which Apple ID is signed in to your device
If you're signed in on your device with an Apple ID that you don't recognize, use these steps to sign out, then back in with a different Apple ID. To make sure that you're signed in to Apple IDs that only you control or trust, you can check the following settings on each of your devices:
Follow steps below:1. https://heavenlyherbal.weebly.com/photo-management-software-mac-2017.html. Yet, with the discontinuity of iPhoto and Aperture, Apple develops Apple Photo as and Aperture to manage and sync your iPhone iPad iPod photos.Photos app arranges your photos in specific order. Launch you Photos App on Mac and it shows an import screen.3. And you are also allowed to create your own private albums, transfer photos from iPhone to Mac via Photos app together with iCloud Photos Library.? Connect your iPhone to your Mac with a USB cable and unlock your iPhone.2.
Download road rash game setup. Oct 07, 2019 Choose Apple menu About This Mac. This opens an overview of your Mac, including your Mac model, processor, memory, serial number, and version of macOS. To see the greater detail provided by the System Information app, click the System Report button. To open System Information directly, press and hold the Option key and choose Apple menu System Information. Why can t my mac find its system software windows 10. Jun 24, 2015 A folder with a question mark kept flashing. According to Apple Support page, this means that my Mac can't find the system software it needs to start up. After following some instructions I got to the Disk Utilities area and realised that my Macintosh HD OS X disk is missing. So I can't repair, erase or reinstall anything.
iPhone, iPad, or iPod touch:
- Settings > [your name]
- Settings > [your name] > iTunes & App Store
- Settings > Messages > Send & Receive
- Settings > FaceTime
Mac:
Some customers may get this error when clicking install button from their My Account page:' An error has occurred. Please try again later.' Microsoft office not activating on mac. We can't move on to the next step.
- System Preferences > Apple ID
- System Preferences > Internet Accounts
- Messages > Preferences > Accounts
- Facetime > Preferences > Settings
- Mail > Preferences > Accounts
- Calendar > Preferences > Accounts
You should also check iCloud for Windows, your AirPort Time Capsule or other AirPort Base Station, and your Apple TV (for iCloud Photos or Home Sharing). Hack rar password protected file.
Make sure your Apple ID is secure
Because you use your Apple ID for so many Apple products and services, you should make sure that your Apple ID is as secure as possible. You should be the only person who knows your password and can sign in with your Apple ID. If someone you don’t know or don’t trust can sign in with your Apple ID, your account is not secure.
Your Apple ID might not be secure for the following reasons:
- Someone else created an Apple ID on your behalf, or you’re using an Apple ID that was already signed in when you received your device.
- You’re sharing an Apple ID with family or friends. Your Apple ID is your personal account. If you want to share purchases with a family member, use Family Sharing. With Family Sharing, you can share a calendar, photos, reminders, and more without sharing your Apple ID.
- You don’t recognize the Apple ID that is signed in on your device.
- You shared your password with someone else intentionally or unintentionally. For example, someone else selected your password for you, you told someone your password, or you entered your password on a phishing site.
- You don't have control of the email address or phone number associated with your Apple ID.
- Your password is weak or is compromised.
- You share your devices with someone else, your devices are not protected by a passcode, or your passcode is easy to guess.
If any of the above are true, you should reset your password as soon as possible and review your account information.
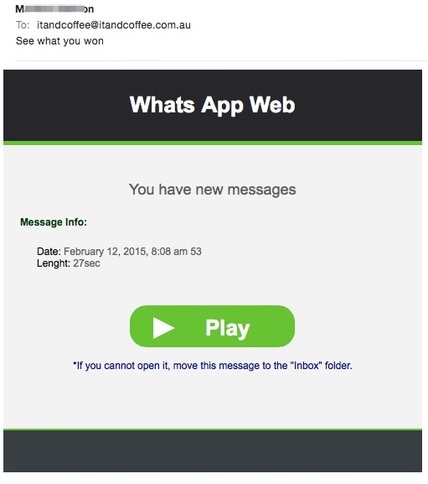
Spammers use a variety of methods to send spam, but the use of hacked legitimate user’s email accounts is booming. Cobol db2 programming guide.
According to Verizon's 2017 Data Breach Investigations Report, 1 in 131 emails contained malware in 2016, the highest rate in 5 years. In addition, the amount of spam spewing into inboxes globally is at its highest rate since 2015. This is related to malware like Emotet and Trickbot stealing email addresses to feed spam campaigns.
As positive as crackdowns on other channels have been, one outcome is that spammers have scrambled to shift the focus of some of the recent larger malware outbreaks and phishing attacks to now be about acquiring enough compromised email accounts to make spamming viable. This includes email accounts like yours.
How was my email hacked?
Your computer was most likely compromised in one of four ways:
New outlook mac. You do not have up-to-date security software installed.
Your passwords are weak and easily hacked.
You clicked on a malicious link in an email, IM conversation, or on a social networking site, or webpage.
You downloaded a game, video, song, or attachment with malicious scripts or files attached
What to do after your email was hacked
When your email account is hacked, here are several steps you need to take to fix the problem and prevent it from happening again:
Mac Email Hacked Iphone
- Check (and update) your computer’s security. Most hackers collect passwords using malware that has been installed on your computer (or mobile phone if you have a smartphone). No matter which operating system you use, be sure your anti-virus and anti-malware programs are up to date. Choose the setting that will automatically update your computer when new security fixes are available. If you’re already using an antivirus program, run an end-to-end scan of your computer.
Look to see that all operating system updates are also installed. To find these, type ’(the name of your operating system) and updates’ into your search engine. Set your computer to update automatically so that you get protection from new attacks as soon as possible. Change your password and make it stronger. Do this after your anti-virus and anti-malware programs are updated or the hackers may collect your new password as well.
- Strong passwords do not have to be hard to remember, they just have to be hard to guess.
- Make your password at least 10 characters long, and use capital letters, lower case letters, numbers, and symbols.
- Do not use information about yourself or someone close to you (including your dog or cat!) like name, age, or city.
- Do not use words that can be found in a dictionary, these are easy for hackers to break, even if you spell them backward.
- Text messaging shortcuts can help make strong, memorable password creation easier. For example L8rL8rNot2Day! translates to later, later, not today.
- Studies show that the average email account has 130 password-protected accounts linked to it, so it's no wonder passwords often aren't as secure as they should be. A password manager can help you keep them in order and encrypted.
- Send an email to your contacts saying you were hacked. When an email comes from someone you know you are more likely to open it and click on links within it - even if the subject is weird. Help stop the spread of the malware by warning those in your contact list to be cautious of any email sent by you that doesn’t seem right and to not click on the links.
- Smarten up about spam, phishing, and scams. Spam comes at us from all angles; in the mailbox in front of your home (junk mail) in your email inbox, via IM, social networking sites, chats, forums, websites, and sadly, now also on your phone. Now more than ever, it is important to be on the lookout for phishing scams.
- You do not have a rich uncle you’ve never heard of in some foreign country trying to send you money. You have not won the lottery. No stranger is going to give you money for any reason. No hot babe is lonely and waiting for your response. The only things you’ll get via an unsolicited pharmacy offer is ripped off or an infection (on your computer or phone). If there really was a miracle weight loss cure, it would be front page news and on every TV station.
- No reputable bank or company is ever going to ask you to ’authenticate’ information online. And if you get an email with a link to one of these sites, don’t use it; instead, use your search engine to find the site yourself, and then log in. If the message was legitimate, the message will be waiting for you in your account.
- Validate the legitimacy of any program, game, app, or video before downloading it. Of the millions of new or updated mobile apps analyzed by Webroot in 2017, 32% were determined to be malicious in nature. If the content is pirated, free, or comes to you anonymously, assume it has malware. Only download content that you have read good reviews about from sites you can trust.
- Change your security question(s). If your email account was hacked from a device or location not matching your normal usage patterns, it's possible the cybercriminal needed to correctly answer a security question. If your question and answer are common (Question: What is your dog's name? Answer: Spot), that may not have been a difficult challenge.
Consider adopting two-factor authentication. Many email providers offer two-factor authentication (2FA) as an additional security measure. This method requires both a password and some other form of identification, such as a biometric or a mobile phone number, to access an account.
My Mac Has Been Hacked
As mentioned, it's fairly common for malware to be the avenue through which an email account is hacked. Having an up-to-date internet security solution is the essential first step in establishing online safety and ensuring your email isn't hacked. Webroot offers a full line of internet security solutions for the home to keep your email password out of the hands of hackers.